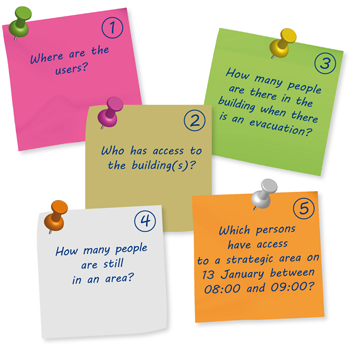
Philosophy. The first stage involves physically closing off all access to a building or site. The next stage is to choose a username for each user and assign authorised access areas. The access control system needs to answer the following questions:
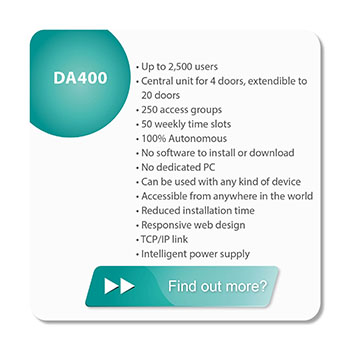
| The fundamental objectives of access control are therefore to limit access to authorised individuals and to ensure traceability for all events, along with a filtering tool to present reports. Readers and usernames: • 125 Khz proximity, Mifare-Desfire, Legic • Mobile telephone and NFC tablet NFC (Android 4) • Biometrics: fingerprints, hand morphology, face recognition • Any type of reader • Keypad reade Centralised real-time system: • IP and/or RS485 solution • Online door fitting or cylinder (Aperio) Beelock independent lock: • System with access rights on the pass • The pass consolidates all the events for that user in less than 24 hours • 4095 locks | ||||||||||
Access control

With a username, only those authorised to access an area can do so. Traceability and statistical analysis are an integral part of a site's security strategy.